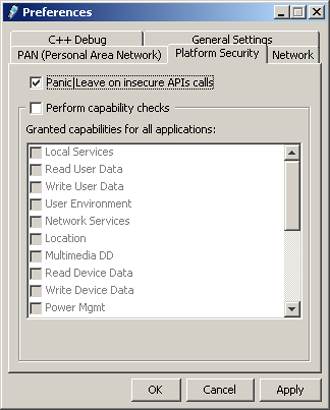
Platform Security tab
The Platform Security tab contains options that configure the Symbian OS security model of the emulator. Platform Security (PlatSec) options determine how the operating system handles applications which require and use the restricted capabilities of Symbian OS.
Note: In a device, these settings are fixed and cannot be changed. Insecure APIs are always disabled, and Platform Security is always enforced.
In the top part of the dialog there are three checkboxes with the following functionality:
Panic|Leave on insecure APIs calls - Disables EKA1 kernel legacy APIs which are crippled by process isolation introduced by the EKA2 kernel. See below for a list of APIs and functions that are removed completely or have limited functionality if this option is checked.
Perform Capability checks - If this option is checked, Symbian OS enforces capability checking and prevents applications from accessing restricted APIs if they do not have the required capabilities. If this option is not checked, Symbian OS only warns (with debug messages) if an application accesses a restricted API without permission, but lets the API call go through anyway.
The bottom part of the tab contains a list of restricted capabilities provided by Symbian OS for applications. By checking or unchecking the checkbox of a capability in the list you can grant or ungrant it for all applications. These checks have effect on only those applications which do not have the specified capability compiled in. See Capabilities table below for descriptions of capabilities.
Changes are approved by clicking the OK or Apply button. Changes require the emulator to be rebooted to take effect.
Capabilities
|
Capability |
Description |
|---|---|
|
|
Access to remote services in the close vicinity of the phone. |
|
|
Read access to data confidential to the phone user. |
|
|
Write access to data confidential to the phone user. |
|
|
Access to live confidential information about the user and his/her immediate environment. |
|
|
Access to remote services without any restriction on its physical location. |
|
|
Access to end user location information. |
|
|
Access to multimedia device drivers. |
|
|
Read access to software settings and other device data. |
|
|
Write access to software settings and other device data. |
|
|
Right to kill any process in the system or to switch machine state (turn device off). |
|
|
Differentiates normal applications from trusted applications. |
|
|
Right to a server to register with a protected name. |
|
|
Right to modify or access network protocol controls. |
|
|
Right to generate and capture sw key and pen events. |
|
|
Access to DRM protected content. |
|
|
Access to logical device drivers. |
|
|
Access to /sys and /resource directories in terminal. |
|
|
Access to communication device drivers. |
|
|
Right to do disk administration. |
|
|
Visibility to all files in the system and extra write access to files under private. |